- Keytool Generate Self Signed Certificate With Private Key Search
- What Is A Self Signed Certificate
- Keytool Generate Certificate And Private Key
- Keytool Generate Self Signed Certificate With Private Key West
To Create a CSR with keytool and Generate a SignedCertificate for the Certificate Signing Request
This will create a keystore.jks file containing a private key and your sparklingly fresh self signed certificate. Now you just need to configure your Java application to use the.jks file. If you are using Tomcat, you can follow our Tomcat SSL Installation Instructions. To Create a CSR with keytool and Generate a Signed Certificate for the Certificate Signing Request Perform the following operations from the command line. Keytool –keystore clientkeystore –genkey –alias client Enter keystore password: javacaps What is your first and last name? I would like to export my private key from a Java Keytool keystore, so I can use it with openssl. I would like to export my private key from a Java Keytool keystore, so I can use it with openssl. How can I do that? It makes perfect sense to re-use the same private key if it matches a certificate that has been signed by a CA, for example. Apr 16, 2015 In most cases you must use a CA verified certificate but you can also use a self signed cert to secure your java app. Steps to create a Self Signed Certificate using Java Keytool Step 1. Jul 31, 2009 To generate a self-signed certificate, you need a program called “keytool”, which is supplied with any version of the Java SDK. The instructions below walk through the creation of both the key store and the trust store files for a 1-way SSL configuration with the security keys. Creating a Self-Signed Certificate and a Private Key. Use the keytool utility to create a keystore file that contains a private key and a self-signed certificate that holds a public key. Note: To replace an expired self-signed certificate, delete the existing keystore file, follow the procedure in this topic to create a new self-signed certificate, and then configure SSL on the Tomcat server. However, before you replace an expired self-signed certificate, you must backup your old keystore. It makes perfect sense to re-use the same private key if it matches a certificate that has been signed by a CA, for example (otherwise, the cert would have to be re-issued too), which may happen when changing the implementation of the server (e.g. Java-based server to Apache HTTPD or a reverse proxy).
Perform the following operations from the command line.
Generate the Certificate Signing Request.
Generate a signed certificate for the associated Certificate SigningRequest.
Use the keytool to import the CA certificate into the client keystore.
Use the keytool to import the signed certificate for the associatedclient alias in the keystore.
Caution –The following error will be generated if there is no certificatechain in the client certificate.
This error is because the CA’s certificate was not imported intothe KeyStore first. You must import theCA's certificate (step 4), then import the client.cer file itself to forma certificate chain (step 5).
Now that we have a private key and an associating certificate chainin the KeyStore clientkeystore, we canuse it as a KeyStore for client (adapter)authentication. The only warning is that the CA certificate must be importedinto the trusted certificate store of the web server to which you will beconnecting. Moreover, the web server must be configured for client authentication(httpd.conf for Apache, for example).
Securing your Java application with an SSL certificate can be extremely important. Fortunately, it is (usually) quite simple to do using Java Keytool. Most situations require that you buy a trusted certificate, but there are many cases when you can generate and use a self signed certificate for free.
When to Use a Keytool Self Signed Certificate
An SSL certificate serves two essential purposes: distributing the public key and verifying the identity of the server so users know they aren't sending their information to the wrong server. It can only properly verify the identity of the server when it is signed by a trusted third party. A self signed certificate is a certificate that is signed by itself rather than a trusted authority. Since any attacker can create a self signed certificate and launch a man-in-the-middle attack, a user can't know whether they are sending their encrypted information to the server or an attacker. Because of this, you will almost never want to use a self signed certificate on a public Java server that requires anonymous visitors to connect to your site. However, self signed certificates have their place:
Never use a self signed certificate on an e-commerce site or any site that transfers valuable personal information like credit cards, social security numbers, etc.
- An Intranet. When clients only have to go through a local Intranet to get to the server, there is virtually no chance of a man-in-the-middle attack.
- A Java development server. There is no need to spend extra cash buying a trusted certificate when you are just developing or testing an application.
- Personal sites with few visitors. If you have a small personal site that transfers non-critical information, there is very little incentive for someone to attack the connection.
Just keep in mind that visitors will see a warning in their browsers (like the one below) when connecting to a server that uses a self signed certificate until it is permanently stored in their certificate store.
Generate a Self Signed Certificate using Java Keytool
Now that you know when to use a Keytool self signed certificate, let's create one using a simple Java Keytool command:
- Open the command console on whatever operating system you are using and navigate to the directory where keytool.exe is located (usually where the JRE is located, e.g. c:Program FilesJavajre6bin on Windows machines).
- Run the following command (where validity is the number of days before the certificate will expire):
keytool -genkey -keyalg RSA -alias selfsigned -keystore keystore.jks -storepass password -validity 360 -keysize 2048 - Fill in the prompts for your organization information. When it asks for your first and last name, enter the domain name of the server that users will be entering to connect to your application (e.g. www.google.com)
Keytool Generate Self Signed Certificate With Private Key Search
This will create a keystore.jks file containing a private key and your sparklingly fresh self signed certificate. Now you just need to configure your Java application to use the .jks file. If you are using Tomcat, you can follow our Tomcat SSL Installation Instructions.
For more information on creating a Java Keytool Self Signed Certificate, see the following links:
What Is A Self Signed Certificate
Originally posted on Sat Oct 30, 2010
Save
Keytool Generate Certificate And Private Key
Product key generator microsoft office 2019. Save
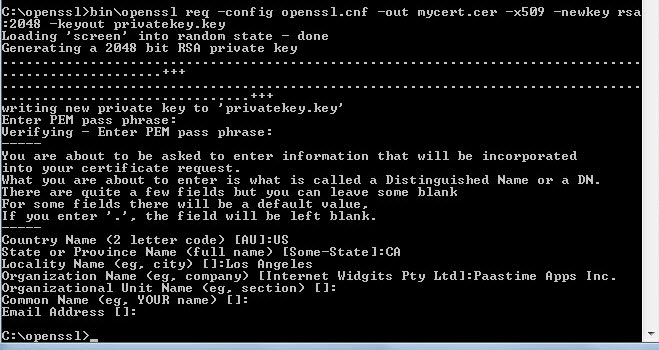
Keytool Generate Self Signed Certificate With Private Key West
Save