- Onboard Secure Cryptographic Key Generation Software
- Onboard Secure Cryptographic Key Generation 1
- Cryptographic Key Management Standards
- Cryptographic Key Management
This section discusses two options to get a trusted X.509 client certificate onto an IoT device for lab testing. Depending on the capabilities of the device, various provisioning-related operations may or may not be supported, including onboard ECDSA key generation, private key import, and X.509 certificate enrollment. Nov 17, 2019 onboard secure cryptographic key generation; onboard secure cryptographic key storage, at least for the top level and most sensitive keys, which are often called master keys; key management; use of cryptographic and sensitive data material, for example, performing encryption or digital signature functions.
A hardware security module (HSM) is a physical computing device that safeguards and manages digital keys for strong authentication and provides cryptoprocessing. These modules traditionally come in the form of a plug-in card or an external device that attaches directly to a computer or network server. A hardware security module contains one or more secure cryptoprocessorchips.[1][2][3]
Contents
History
Humans have tried to establish and maintain confidential lines of communication for millennia, rarely with enduring success. During World War II governments and military organizations invested heavily in encryption systems (cryptographic 'defense') and code breaking (cryptographic 'offense'). However, civilian and commercial adoption of encryption systems lagged considerably, in large part due to legal and regulatory constraints.
As global trade and the financial industry flourished after World War II, and as national economic security became more strategic, commercial exploitation of strong encryption emerged as a national imperative in the United States and in several other countries. In the early 1970s the U.S. National Bureau of Standards (NBS) sponsored a standardization process for cryptographic algorithms to be available for civilian use. IBM submitted its Data Encryption Standard (DES) on a royalty free basis for the NBS's consideration (and U.S. National Security Agency review), and the U.S. declared DES the U.S. commercial symmetric-key encryption algorithm standard in 1977. Within the same year IBM introduced the IBM 3845, the first generally commercially available (i.e., civilian) HSM that was directly attached (via IBM's channel I/O architecture) to general purpose IBM computers, including IBM mainframes. The IBM 3845 included secure key entry devices (cards and PIN pads) for master key loading, random number generation capabilities for seeding, and persistent storage for key materials. IBM introduced enabling software, notably a predecessor to IBM's Integrated Cryptographic Service Facility (ICSF), to allow application programmers to take advantage of the HSM's services. The IBM 3845 helped launch and secure modern electronic banking, such as national and international Automatic Teller Machine (ATM) and payment card networks. IBM quickly introduced a second generation IBM 3845 HSM that supported both DES and TDES. Other vendors then introduced various HSMs, also based initially on DES then TDES.
HSMs have continued to evolve and improve ever since, but many modern HSMs, including IBM's, still broadly resemble the IBM 3845's basic architecture: direct attachment (typically now via dedicated network or bus attachment, sometimes with the HSM embedded), some level of tamper protection (or at least tamper evident packaging) in varying degrees and certification levels, some mechanism for loading and managing key materials with varying levels of trust, random number generation capabilities, persistent storage, and software features (drivers, libraries, etc.) to access the HSM's services from both general purpose and specialized computing environments, including transaction processing systems.
Design
HSMs may have features that provide tamper evidence such as visible signs of tampering or logging and alerting, or tamper resistance which makes tampering difficult without making the HSM inoperable, or tamper responsiveness such as deleting keys upon tamper detection.[4] Each module contains one or more secure cryptoprocessor chips to prevent tampering and bus probing, or a combination of chips in a module that is protected by the tamper evident, tamper resistant, or tamper responsive packaging.
A vast majority of existing HSMs are designed mainly to manage secret keys. Many HSM systems have means to securely back up the keys they handle outside of the HSM. Keys may be backed up in wrapped form and stored on a computer disk or other media, or externally using a secure portable device like a smartcard or some other security token.[5]
Because HSMs are often part of a mission-critical infrastructure such as a public key infrastructure or online banking application, HSMs can typically be clustered for high availability and performance. Some HSMs feature dual power supplies and field replaceable components such as cooling fans to conform to the high-availability requirements of data center environments and to enable business continuity.
A few of the HSMs available in the market have the capability to execute specially developed modules within the HSM's secure enclosure. Such an ability is useful, for example, in cases where special algorithms or business logic has to be executed in a secured and controlled environment. The modules can be developed in native C language, .NET, Java, or other programming languages. Further, upcoming next-generation HSMs[6] can handle more complex tasks such as loading and running full operating systems and COTS software without requiring customization and reprogramming. Such unconventional designs overcome existing design and performance limitations of traditional HSMs. While providing the benefit of securing application-specific code, these execution engines protect the status of an HSM's FIPS or Common Criteria validation.
With the advent of Trusted Execution Environments (TEEs), some claim that HSMs no longer need to depend on proprietary hardware architectures and physical tamper protection. Rather, they can exploit the security properties of the TEE to protect the confidentiality and integrity of both the secret keys and the application code. This enables 'soft HSMs' such as the Fortanix Self-Defending Key Management Service[7] to be deployed using off-the-shelf hardware, virtual machines, and cloud servers while providing similar security guarantees to traditional HSMs. Moreover, such solutions can utilize cloud-native technologies to simplify scaling. There is also the possibility of executing custom code plugins within the TEE. However, these guarantees provided by soft HSMs are not similar to those provided by proprietary hardware architectures and physical tamper protection, and various standards organizations do not accept these arguments.
Security
Due to the critical role they play in securing applications and infrastructure, HSMs and/or the cryptographic modules are typically certified to internationally recognized standards such as Common Criteria or FIPS 140 to provide users with independent assurance that the design and implementation of the product and cryptographic algorithms are sound. The highest level of FIPS 140 security certification attainable is Security Level 4 (Overall), to which only one HSM has been successfully validated as of August 2018.[8] When used in financial payments applications, the security of an HSM is often validated against the HSM requirements defined by the Payment Card Industry Security Standards Council.[9]
Uses
A hardware security module can be employed in any application that uses digital keys. Typically the keys must be of high value - meaning there would be a significant, negative impact to the owner of the key if it were compromised.
The functions of an HSM are:
- onboard secure cryptographic key generation
- onboard secure cryptographic key storage, at least for the top level and most sensitive keys, which are often called master keys
- key management
- use of cryptographic and sensitive data material, for example, performing encryption or digital signature functions
- offloading application servers for complete asymmetric and symmetric cryptography.
HSMs are also deployed to manage transparent data encryption keys for databases and keys for storage devices such as disk or tape.
HSMs provide both logical and physical protection of these materials, including cryptographic keys, from disclosure, non-authorized use, and potential adversaries.[10]
HSMs support both symmetric and asymmetric (public-key) cryptography. For some applications, such as certificate authorities and digital signing, the cryptographic material is asymmetric key pairs (and certificates) used in public-key cryptography.[11] With other applications, such as data encryption or financial payment systems, the cryptographic material consists mainly of symmetric keys.
Some HSM systems are also hardware cryptographic accelerators. They usually cannot beat the performance of hardware-only solutions for symmetric key operations. However, with performance ranges from 1 to 10,000 1024-bit RSA signs per second, HSMs can provide significant CPU offload for asymmetric key operations. Since the National Institute of Standards and Technology (NIST) is recommending the use of 2,048 bit RSA keys from year 2010,[12] performance at longer key sizes is becoming increasingly important. To address this issue, some HSMs now support elliptic curve cryptography (ECC), which delivers stronger encryption with shorter key lengths.
PKI environment (CA HSMs)
In PKI environments, the HSMs may be used by certification authorities (CAs) and registration authorities (RAs) to generate, store, and handle asymmetric key pairs. In these cases, there are some fundamental features a device must have, namely:
- Logical and physical high-level protection
- Multi-part user authorization schema (see Blakley-Shamir secret sharing)
- Full audit and log traces
- Secure key backup
On the other hand, device performance in a PKI environment is generally less important, in both online and offline operations, as Registration Authority procedures represent the performance bottleneck of the Infrastructure.
Card payment system HSMs (bank HSMs)
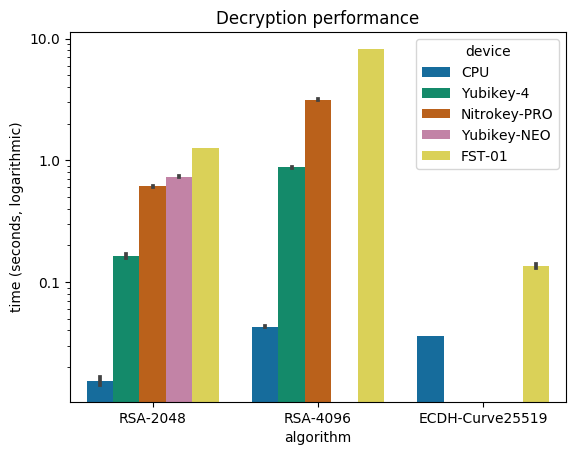
Specialized HSMs are used in the payment card industry. HSMs support both general-purpose functions and specialized functions required to process transactions and comply with industry standards. They normally do not feature a standard API.
Typical applications are transaction authorization and payment card personalization, requiring functions such as:
- verify that a user-entered PIN matches the reference PIN known to the card issuer
- verify credit/debit card transactions by checking card security codes or by performing host processing components of an EMV based transaction in conjunction with an ATM controller or POS terminal
- support a crypto-API with a smart card (such as an EMV)
- re-encrypt a PIN block to send it to another authorization host
- perform secure key management
- support a protocol of POS ATM network management
- support de facto standards of host-host key data exchange API
- generate and print a 'PIN mailer'
- generate data for a magnetic stripe card (PVV, CVV)
- generate a card keyset and support the personalization process for smart cards
The major organizations that produce and maintain standards for HSMs on the banking market are the Payment Card Industry Security Standards Council, ANS X9, and ISO.
SSL connection establishment
Performance-critical applications that have to use HTTPS (SSL/TLS), can benefit from the use of an SSL Acceleration HSM by moving the RSA operations, which typically requires several large integer multiplications, from the host CPU to the HSM device. Typical HSM devices can perform about 1 to 10,000 1024-bit RSA operations/second.[13] Some performance at longer key sizes is becoming increasingly important. To address this issue, some HSMs [14] now support ECC. Specialized HSM devices can reach numbers as high as 20,000 operations per second.[15]
DNSSEC
An increasing number of registries use HSMs to store the key material that is used to sign large zonefiles. An open source tool for managing signing of DNS zone files using HSM is OpenDNSSEC.
On January 27, 2007 deployment of DNSSEC for the root zone officially started; it was undertaken by ICANN and Verisign, with support from the U.S. Department of Commerce.[16] Details of the root signature can be found on the Root DNSSEC's website.[17]
Cryptocurrency wallet
A hardware cryptocurrency wallet is a HSM in the form of a portable device.
See also
Notes and references
- ↑ Ramakrishnan, Vignesh; Venugopal, Prasanth; Mukherjee, Tuhin (2015). Proceedings of the International Conference on Information Engineering, Management and Security 2015: ICIEMS 2015. Association of Scientists, Developers and Faculties (ASDF). p.9. ISBN9788192974279.
- ↑ 'Secure Sensitive Data with the BIG-IP Hardware Security Module'(PDF). F5 Networks. 2012. Retrieved 30 September 2019.
- ↑ Gregg, Michael (2014). CASP CompTIA Advanced Security Practitioner Study Guide: Exam CAS-002. John Wiley & Sons. p.246. ISBN9781118930847.
- ↑ 'Electronic Tamper Detection Smart Meter Reference Design'. freescale. Retrieved 26 May 2015.
- ↑ 'Using Smartcard/Security Tokens'. mxc software. Retrieved 26 May 2015.
- ↑ 'World's First Tamper-Proof Server and General Purpose Secure HSM'. Private Machines. Retrieved 7 March 2019.
- ↑ 'Self-Defending Key Management Service™ (SDKMS) Fortanix'. fortanix.com. Retrieved 2020-03-26.
- ↑ 'Encryption solutions'. Ultra Electronics. Archived from the original on October 18, 2016. Retrieved August 5, 2018.
Ultra also boasts the world’s only network-attached Hardware Security Module (HSM) utilising a cryptographic module that is certified to FIPS 140-2 Level 4 overall.
- ↑ 'Official PCI Security Standards Council Site - Verify PCI Compliance, Download Data Security and Credit Card Security Standards'. www.pcisecuritystandards.org. Retrieved 2018-05-01.
- ↑ 'Support for Hardware Security Modules'. paloalto. Archived from the original on 26 May 2015. Retrieved 26 May 2015.
- ↑ 'Application and Transaction Security / HSM'. Provision. Retrieved 26 May 2015.
- ↑ 'Transitions: Recommendation for Transitioning the Use of Cryptographic Algorithms and Key Lengths'. NIST. January 2011. Retrieved March 29, 2011.
- ↑ F. Demaertelaere. 'Hardware Security Modules'(PDF). Atos Worldline. Archived from the original(PDF) on 6 September 2015. Retrieved 26 May 2015.
- ↑ 'Barco Silex FPGA Design Speeds Transactions In Atos Worldline Hardware Security Module'. Barco-Silex. January 2013. Retrieved April 8, 2013.
- ↑ 'SafeNet Network HSM - Formerly Luna SA Network-Attached HSM'. Gemalto. Retrieved 2017-09-21.
- ↑ 'ICANN Begins Public DNSSEC Test Plan for the Root Zone'. www.circleid.com. Retrieved 2015-08-17.
- ↑ Root DNSSEC
External links
| Wikimedia Commons has media related to Hardware security modules. |
Related Research Articles
A secure cryptoprocessor is a dedicated computer-on-a-chip or microprocessor for carrying out cryptographic operations, embedded in a packaging with multiple physical security measures, which give it a degree of tamper resistance. Unlike cryptographic processors that output decrypted data onto a bus in a secure environment, a secure cryptoprocessor does not output decrypted data or decrypted program instructions in an environment where security cannot always be maintained.

A smart card, chip card, or integrated circuit card (ICC) is a physical electronic authorization device, used to control access to a resource. It is typically a plastic credit card-sized card with an embedded integrated circuit (IC) chip. Many smart cards include a pattern of metal contacts to electrically connect to the internal chip. Others are contactless, and some are both. Smart cards can provide personal identification, authentication, data storage, and application processing. Applications include identification, financial, mobile phones (SIM), public transit, computer security, schools, and healthcare. Smart cards may provide strong security authentication for single sign-on (SSO) within organizations. Numerous nations have deployed smart cards throughout their populations.
In cryptography, zeroisation is the practice of erasing sensitive parameters from a cryptographic module to prevent their disclosure if the equipment is captured. This is generally accomplished by altering or deleting the contents to prevent recovery of the data. When encryption was performed by mechanical devices, this would often mean changing all the machine's settings to some fixed, meaningless value, such as zero. On machines with letter settings rather than numerals, the letter 'O' was often used instead. Some machines had a button or lever for performing this process in a single step. Zeroisation would typically be performed at the end of an encryption session to prevent accidental disclosure of the keys, or immediately when there was a risk of capture by an adversary.
Key management refers to management of cryptographic keys in a cryptosystem. This includes dealing with the generation, exchange, storage, use, crypto-shredding (destruction) and replacement of keys. It includes cryptographic protocol design, key servers, user procedures, and other relevant protocols.
The Federal Information Processing Standard (FIPS) Publication 140-2, is a U.S. government computer security standard used to approve cryptographic modules. The title is Security Requirements for Cryptographic Modules. Initial publication was on May 25, 2001 and was last updated December 3, 2002.
The IBM 4758 PCI Cryptographic Coprocessor is a secure cryptoprocessor implemented on a high-security, tamper resistant, programmable PCI board. Specialized cryptographic electronics, microprocessor, memory, and random number generator housed within a tamper-responding environment provide a highly secure subsystem in which data processing and cryptography can be performed.
In Microsoft Windows, a Cryptographic Service Provider (CSP) is a software library that implements the Microsoft CryptoAPI (CAPI). CSPs implement encoding and decoding functions, which computer application programs may use, for example, to implement strong user authentication or for secure email.
The Microsoft Windows platform specific Cryptographic Application Programming Interface is an application programming interface included with Microsoft Windows operating systems that provides services to enable developers to secure Windows-based applications using cryptography. It is a set of dynamically linked libraries that provides an abstraction layer which isolates programmers from the code used to encrypt the data. The Crypto API was first introduced in Windows NT 4.0 and enhanced in subsequent versions.
In computing, Network Security Services (NSS) comprises a set of libraries designed to support cross-platform development of security-enabled client and server applications with optional support for hardware TLS/SSL acceleration on the server side and hardware smart cards on the client side. NSS provides a complete open-source implementation of cryptographic libraries supporting Transport Layer Security (TLS) / Secure Sockets Layer (SSL) and S/MIME. Previously tri-licensed under the Mozilla Public License 1.1, the GNU General Public License, and the GNU Lesser General Public License, NSS upgraded to GPL-compatible MPL 2.0 with release 3.14.
Disk encryption is a technology which protects information by converting it into unreadable code that cannot be deciphered easily by unauthorized people. Disk encryption uses disk encryption software or hardware to encrypt every bit of data that goes on a disk or disk volume. It is used to prevent unauthorized access to data storage.
Onboard Secure Cryptographic Key Generation Software
The IBM 4764 Cryptographic Coprocessor is a secure cryptoprocessor that performs cryptographic operations used by application programs and by communications such as SSL private key transactions associated with SSL digital certificates. Each coprocessor includes a tamper-responding hardware security module (HSM) that provides secure storage for storing master keys and other sensitive data. The HSM has been certified to meet FIPS 140-2 Level 4 security requirements. The coprocessor is supported on all IBM server platforms including System z (mainframe), System i, System p, and System x. On System z, it is called the 'Crypto Express2'.
OpenDNSSEC is a computer program that manages the security of domain names on the Internet. The project intends to drive adoption of Domain Name System Security Extensions (DNSSEC) to further enhance Internet security.
Arxan Technologies is an American technology company specializing in Application Attack Prevention and Self-Protection solution for IoT, Mobile, and other applications. The company reports that applications secured by it are running on over 500 million devices. Arxan solutions are used to protect applications across a range of industries, including: Mobile Payments & Banking, Automotive IoT, Healthcare IoT, Gaming, and High-Tech. Arxan's security products are used to protect the confidentiality of applications and the integrity of applications.
Utimaco Atalla, founded as Atalla Technovation and formerly known as Atalla Corporation or HP Atalla, is a security vendor, active in the market segments of data security and cryptography. Atalla provides government-grade end-to-end products in network security, and hardware security modules (HSMs) used in automated teller machines (ATMs) and Internet security. The company was founded by Egyptian engineer Mohamed M. Atalla in 1972. Atalla HSMs are the payment card industry's de facto standard, protecting 250million card transactions daily as of 2013, and securing the majority of the world's ATM transactions as of 2014.
Nitrokey is an open source USB key to enable secure encryption and signing of data. The secret keys are always stored inside the Nitrokey which protects against malware and attackers. A user-chosen PIN and a tamper-proof smart card protect the Nitrokey in case of loss and theft. The hardware and software of Nitrokey are available as open source, free software and open hardware which enables independent parties to verify the security of the device. Nitrokey is supported on Microsoft Windows, Linux, and macOS.
Hardware-based encryption is the use of computer hardware to assist software, or sometimes replace software, in the process of data encryption. Typically, this is implemented as part of the processor's instruction set. For example, the AES encryption algorithm can be implemented using the AES instruction set on the ubiquitous x86 architecture. Such instructions also exist on the ARM architecture. However, more unusual systems exist where the cryptography module is separate from the central processor, instead being implemented as a coprocessor, in particular a secure cryptoprocessor or cryptographic accelerator, of which an example is the IBM 4758, or its successor, the IBM 4764. Hardware implementations can be faster and less prone to exploitation than traditional software implementations, and furthermore can be protected against tampering.
/age-of-empires-3-product-key-generator.html. The IBM 4765 PCIe Cryptographic Coprocessor is a hardware security module (HSM) that includes a secure cryptoprocessor implemented on a high-security, tamper resistant, programmable PCIe board. Specialized cryptographic electronics, microprocessor, memory, and random number generator housed within a tamper-responding environment provide a highly secure subsystem in which data processing and cryptography can be performed.
Onboard Secure Cryptographic Key Generation 1
The IBM 4767 PCIe Cryptographic Coprocessor is a hardware security module (HSM) that includes a secure cryptoprocessor implemented on a high-security, tamper resistant, programmable PCIe board. Specialized cryptographic electronics, microprocessor, memory, and random number generator housed within a tamper-responding environment provide a highly secure subsystem in which data processing and cryptography can be performed. Sensitive key material is never exposed outside the physical secure boundary in a clear format.
Cryptographic Key Management Standards
The IBM 4768 PCIe Cryptographic Coprocessor is a hardware security module (HSM) that includes a secure cryptoprocessor implemented on a high-security, tamper resistant, programmable PCIe board. Specialized cryptographic electronics, microprocessor, memory, and random number generator housed within a tamper-responding environment provide a highly secure subsystem in which data processing and cryptography can be performed. Sensitive key material is never exposed outside the physical secure boundary in a clear format.
The IBM 4769 PCIe Cryptographic Coprocessor is a hardware security module (HSM) that includes a secure cryptoprocessor implemented on a high-security, tamper resistant, programmable PCIe board. Specialized cryptographic electronics, microprocessor, memory, and random number generator housed within a tamper-responding environment provide a highly secure subsystem in which data processing and cryptography can be performed. Sensitive key material is never exposed outside the physical secure boundary in a clear format.
Cryptographic Key Management
Text is available under the CC BY-SA 4.0 license; additional terms may apply.
Images, videos and audio are available under their respective licenses.